Privacy
A place to discuss privacy and freedom in the digital world.
Privacy has become a very important issue in modern society, with companies and governments constantly abusing their power, more and more people are waking up to the importance of digital privacy.
In this community everyone is welcome to post links and discuss topics related to privacy.
Some Rules
- Posting a link to a website containing tracking isn't great, if contents of the website are behind a paywall maybe copy them into the post
- Don't promote proprietary software
- Try to keep things on topic
- If you have a question, please try searching for previous discussions, maybe it has already been answered
- Reposts are fine, but should have at least a couple of weeks in between so that the post can reach a new audience
- Be nice :)
Related communities
much thanks to @gary_host_laptop for the logo design :)
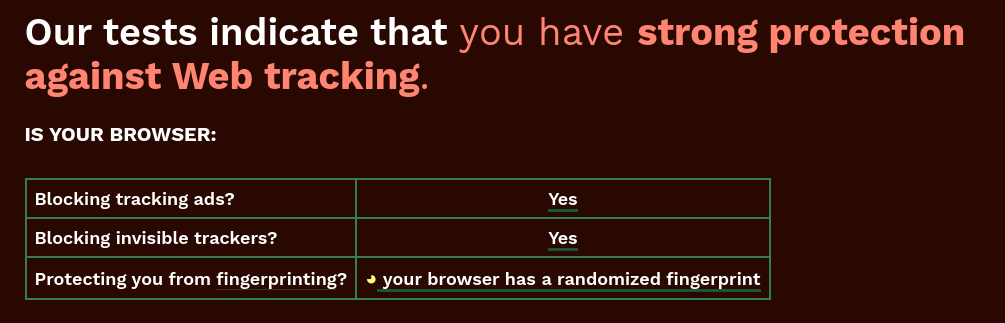
You don't want a randomised fingerprint, as that is relatively unique among a sea of fingerprints [1]. What you want is a fingerprint that's as similar to everyone else (generic) as possible; that's what Firefox's resist fingerprinting setting aims to do, and what the Tor browser does.
[1] There are many values you can't change, so the randomisation of the ones you can change could end up making you more unique ... think of it like having your language set to french but are based in the USA — that language setting can't uniquely identify the French in france, but will stick out like a sore thumb if set in shitsville Idaho. It's likely the same if you use firefox but have your user agent set to chrome; that's more rare and unique than not changing the user agent at all.
No, that's absolutely incorrect. You want a new fake fingerprint every single time someone asks your browser for your information. You want it to lie about your plugins, user agent, your fonts and your screen size. Bonus if you use common values, but not necessary.
The randomized data they're providing isn't static and it isn't the same from session to session.
100% White noise is a far better obfuscation than a 40% non-unique tracking ID. Yes, your data is lumped in with 47 million other users, but used in conjunction with static pieces of your data you become uncomfortably identifiable.
The whole point of the poster above is that you can't ramdomise 100%
Yeah... I don't know why a bunch of privacy bros think they know better than the CS and cryptography PhD's of the Tor project; the most advanced and complex privacy and anonymity preserving project in computing history.
this is the correct answer
Yes. Brave focuses on providing random data points each time it's asked (e.g. screen size). A hardened Firefox will try to provide a generic fingerprint.
Apples to oranges more or less, I'm unaware of any proof that one or the other is considerably better across the board. Though my gut does tell me that randomization is a lot better in the specific situation of regularly signing in and out of accounts.
mullvad browser which is a TOR browser fork, seems to defeat fingerprint.com per-session.
brave strict fingerprint protection on its own actually does not even do this afaik
I believe that Firefox has a mechanism where millions of users all have the same fingerprint, which makes the whole concept of browser fingerprinting useless.
Catch is you have to enable it manually
Purged by creator
It's far better to use this site: fingerprint.com/demo
they are one of the largest actual/commercial vendors of fingerprinting software. their business is to track you.
please try it with brave and post your results. i could be wrong but last time i checked brave failed this test. arkenfox doesn't even allow the tracking to load which I consider a pass although you could argue that just because the results don't load doesn't mean they aren't able to track you in some way