Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
view the rest of the comments
Are you refering locations for vulnerability disclosure or are you more referring to bug bounty?
Fair enough
I'm not the commenter but I can take a guess - I would assume "data source" refers to a machine readable database or aggregator.
Making the system capable of turning off a generic external service in an automated way isn't necessarily trivial, but it's doable given appropriate systems.
Knowing when to turn a service off is going to be the million dollar question. It not only has to determine what the backend application version is during its periodic health check, it also needs to then make an autonomous decision that a vulnerability exists and is severe enough to take action.
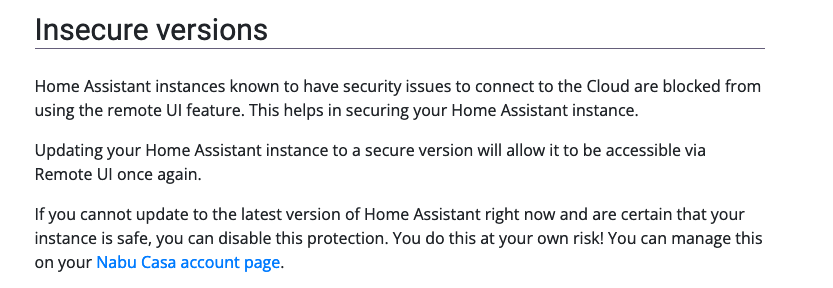
Home Assistant probably provides a "safe list" of versions that instances regularly pull down and automatically disconnect if they determine themselves to be affected, or, of the remote UI connection passes through the Home Assistant Central servers, the Central servers could maintain that safety database and off switch. (Note - I don't have a home assistant so I can't check myself)
I think this is how home assistant handles it. When they put out a cve they can update the insecure version list which makes nabucasa refuse remote forwarding (until you update).
Initially I was just thinking if a open-source project is on github and uses the security disclosure feature if it would be possible to pull data from it and disable remote acess (either by auto shutting down the service or simply disabling routing on a reverse proxy).
Having a system that does without a security disclosure list from a project maintainer would be far mor difficult like having the proxy disable one of your services if it detects a vulnerability in a dependency.