Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
view the rest of the comments
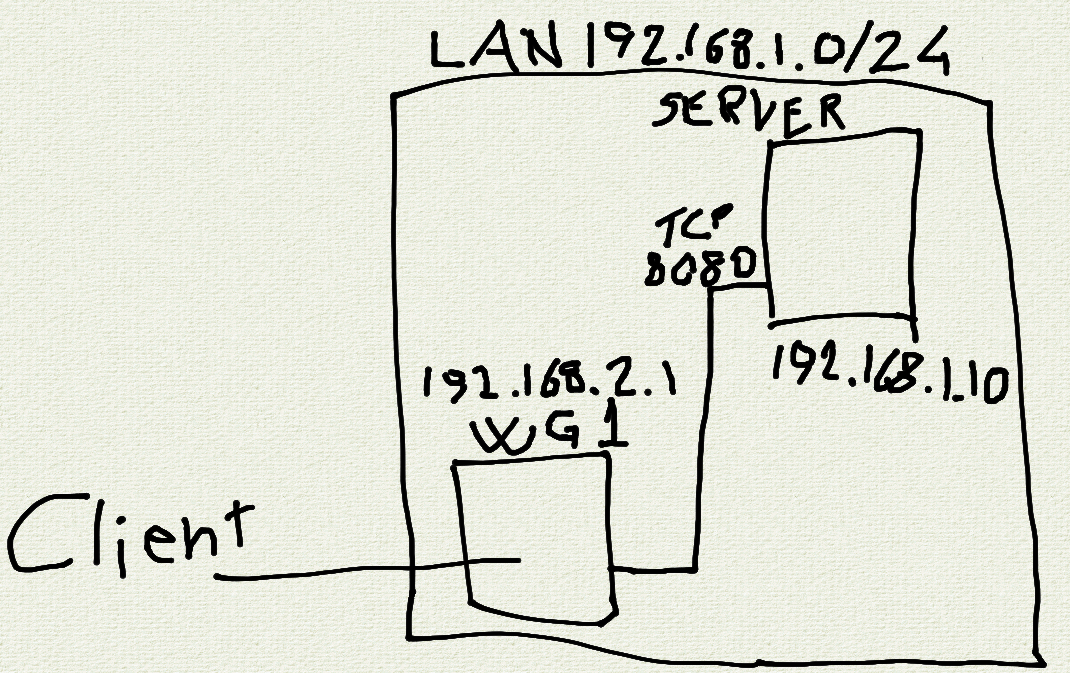
You don't really need forwarding as you don't need NAT here.
A part of the filtering can be done by wireguard by setting the allowed IPs correctly. Just check if only one service is listening on the server port you'll allow.
Now a question: all without tls right? ;)
Could you elaborate what you mean with setting the allowed IPs? Yes, without tls.
Why the downvote?
Apologies for the delay. On the VPN termination point, you have to set the allowed IP addresses. On the case of a client, a /32 is enough. It means that only this IP would be receiving responses. A client with a different IP address would be able to inly send packets, not to get any back, thus not able to get a TCP session. I think it is enough and rhat no additional FW rule is needed.
Don't worry, there's no deadline here. I'm not sure I got it so I'll try to explain what I understood. You're saying that I have to set a single IP address for the client, and allow that single address to connect to service on port 8080 on 192.168.10.1 in the firewall, right? I'm not too confident in my ability to configure the firewall, so I thought that completely isolate the subnet 192.168.2.0 and then forward a single port to it was the safe choice.