Linux
From Wikipedia, the free encyclopedia
Linux is a family of open source Unix-like operating systems based on the Linux kernel, an operating system kernel first released on September 17, 1991 by Linus Torvalds. Linux is typically packaged in a Linux distribution (or distro for short).
Distributions include the Linux kernel and supporting system software and libraries, many of which are provided by the GNU Project. Many Linux distributions use the word "Linux" in their name, but the Free Software Foundation uses the name GNU/Linux to emphasize the importance of GNU software, causing some controversy.
Rules
- Posts must be relevant to operating systems running the Linux kernel. GNU/Linux or otherwise.
- No misinformation
- No NSFW content
- No hate speech, bigotry, etc
Related Communities
Community icon by Alpár-Etele Méder, licensed under CC BY 3.0
Lists of things not to do:
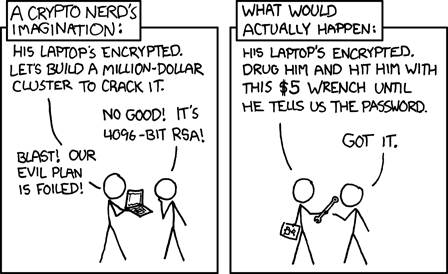
- (NEW!) Go through airport security with an encrypted laptop, sensitive information and free conference stickers showing your affiliations as an activist. Let airport security confiscate your laptop. Airport security drugs and wrenches you. You give them your laptop password. The police arrests you based on suspicions of terrorism.
Except when your drive is encrypted you can easily destroy its contents. Let's say you're DorkPirate1337 who happens to care about their opsec; you luksEncrypt your drive and have a simple script that runs when a specific USB key is disconnected, triggers luksErase, and then poweroffs. Voila, when the school principal snatches your unlocked laptop while you're in the lib, all your pirated hentai becomes permanently unaccessible whether you give up the password or not. [Edit: the USB key is strapped to your wrist]
Note: luks uses 2 encryption keys, where one is randomly generated and encrypts the actual data, and the second one is given by the user and encrypts the first one; luksErase destroys the luks header containing that first key
If the device get stolen, your drive and its files can be easily read.
Other attacks like malware or ransomware are almost the same if the drive is encrypted or not.
Disk encryption is important for laptops and phones because these devices are frequently stolen. For desktop or servers is still good idea, though.
Thanks a lot for your answer. How would you encrypt a server? Typing a password every time it boots isn't possible for me, since I would need a monitor for my headless server.
That's why it's not always an option.
Some servers have some kind remote console hardware, with their own security issues.
Your "threat model" is important too. Do you expect that server to get stolen? If it happens, is there critical data that should not leak?
Maybe you need to encrypt a directory, and not the whole drive.
My threat model isn't high. Just normal stuff everyone has, but that would be disadvantagely if someone else got them.
It's more if a precautionary measure. It doesn't have to be super safe, but better than nothing.
Is this for your home? If it is, you don't really have to worry about someone stealing your desktop. If someone breaks into your home, they're looking for quick cash and jewelry and TVs. They're not going to bother stealing your server to dig through files for something usable.
I've had quite a bad experience with police for example.
30 cops raided my home because of something trivial (I ordered a bit of non-psychoactive CBD-weed, which is, even in the most restrictive country you can imagine, ridiculous).
Of course, I got the whole experience-pack, including strip searches and confiscating all electronics.
Even though I believe them getting hold of any data wouldn't have changed much, I'm still glad I had my devices encrypted.
Just knowing they didn't see my cringy pictures of my teeny-me, where I discovered Snapchat filters, is a big relief. 😅
Yeah... that traumatized me a bit and maybe that's the reason I'm worrying.
Also, you could never know what will happen in the future. Maybe my GF will turn crazy tomorrow and use those embarrassing pictures against me. Who knows?
I believe everyone should use encryption, even if they don't have much to hide...
Oh that's a really good point. Don't trust the cops, keep everything encrypted.
Way safer in those situations.
You can use SSH for unlocking: https://www.cyberciti.biz/security/how-to-unlock-luks-using-dropbear-ssh-keys-remotely-in-linux/
Either self-encrypting drives (if you trust the OEM encryption) or auto-unlock with keys in the TPM: https://wiki.archlinux.org/title/Trusted_Platform_Module#Data-at-rest_encryption_with_LUKS
I use Luks/Tang to unlock the server at boot from another computer that is always on too. If that one is down I’ll need to type it or power the other PC on, but otherwise it auto decrypts for me as long as I’m on the same network.
If Windows, use BitLocker.
If Linux, use LUKS but you need to enter the passphrase at boot, you can securely put the key in TPM2 I think (à la Windows) but it may be complicated to setup, or just seal the phrase in TPM2 but if you boot on grub you can break grub and replace init with a shell in boot option and have access to the system I think :-/ but a simple crackhead thief would not understand that.
You can also have the key on a USB key, but if on the server and the server get stolen, it's useless. You can setup a "anywhereUSB" and have your USB key in another room/place, etc, there is others possibilities.
I wanted to unlock with bluetooth but having the bluetooth HW driver and stack in initramfs was nightmarish a little bit :-/
One option may be a hardware security key. Here is an example: https://www.endpointdev.com/blog/2022/03/disk-decryption-yubikey/
If the risk of physical data theft is high, your data is at risk. If the risk of physical access to you machine is rather low, encryption might actually increases the risk of losing your data simply by the chance of losing the means to access your data (forgotten passphrase, lost hardware key...).
It might also be harder to recover picies if the hard drive fail partially. However, many use SSD now, might be a different story there.
You are relying 100% on physical security. If nobody can take your drive or physically operate your computer, it is safe.
If I could boot a USB stick on your machine, or pull the drive, accessing your data would be trivial.
Somebody can take your disk, easily mount filesystem, and read everything.
I think you mean my data.
our data
I like your thinking, comrade
An encrypted hard drive means that someone cannot physically steal your hard drive and read its contents.
Encryption-at-rest is generally moot against RCE exploits, because your OS will happily decode files that your programs have permission to read.
That said, on modern systems, encryption is cheap. So set it up if you can.
Edit: I replied to the original post.
Community in the text?
Crosspost. Click on it and you'll land on my original post.
I didn't want to duplicate it. You can always suggest me how to make the crosspost more visible, I just did it how my client set it up for me.