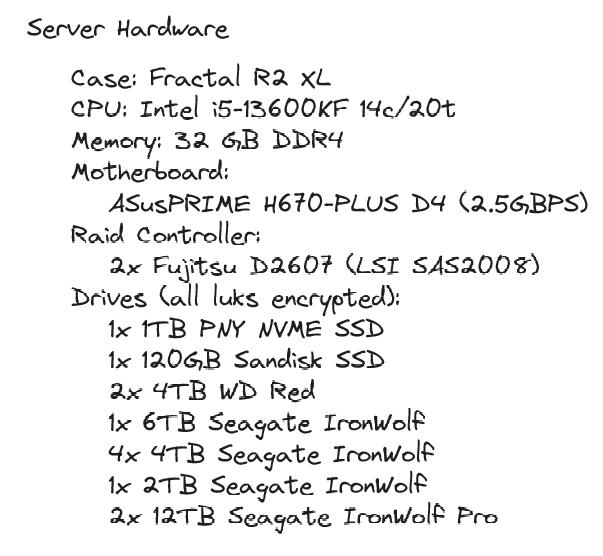
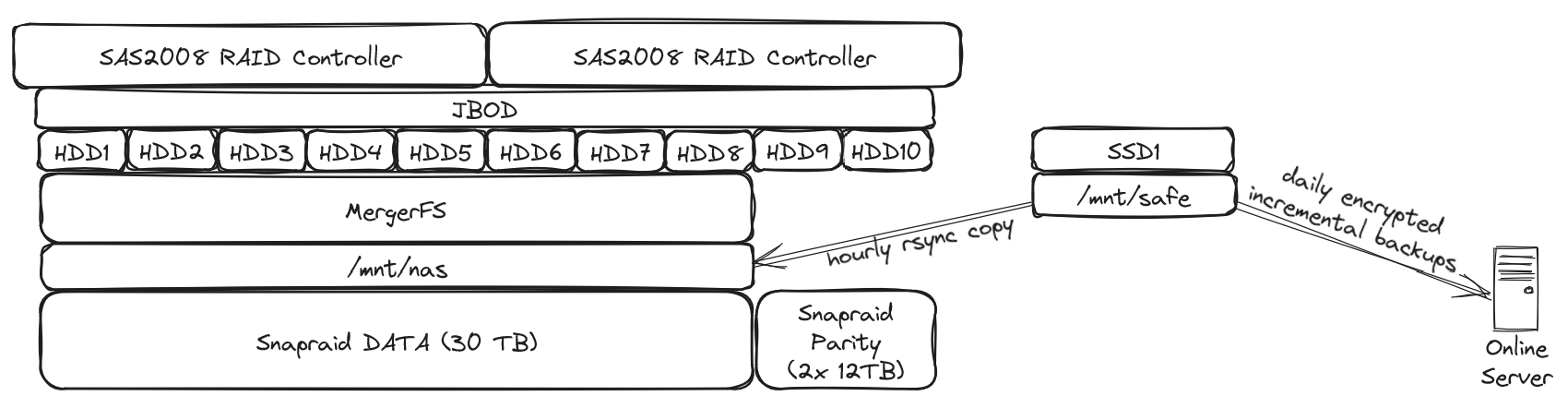
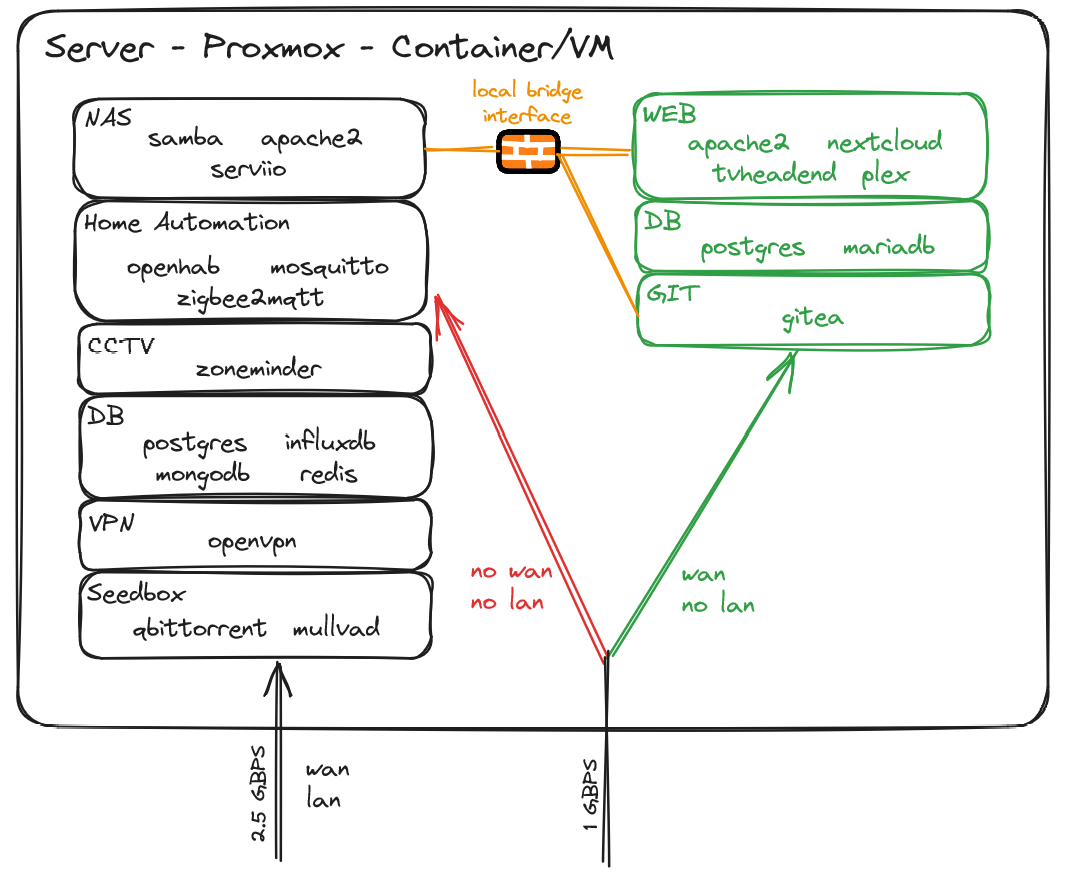
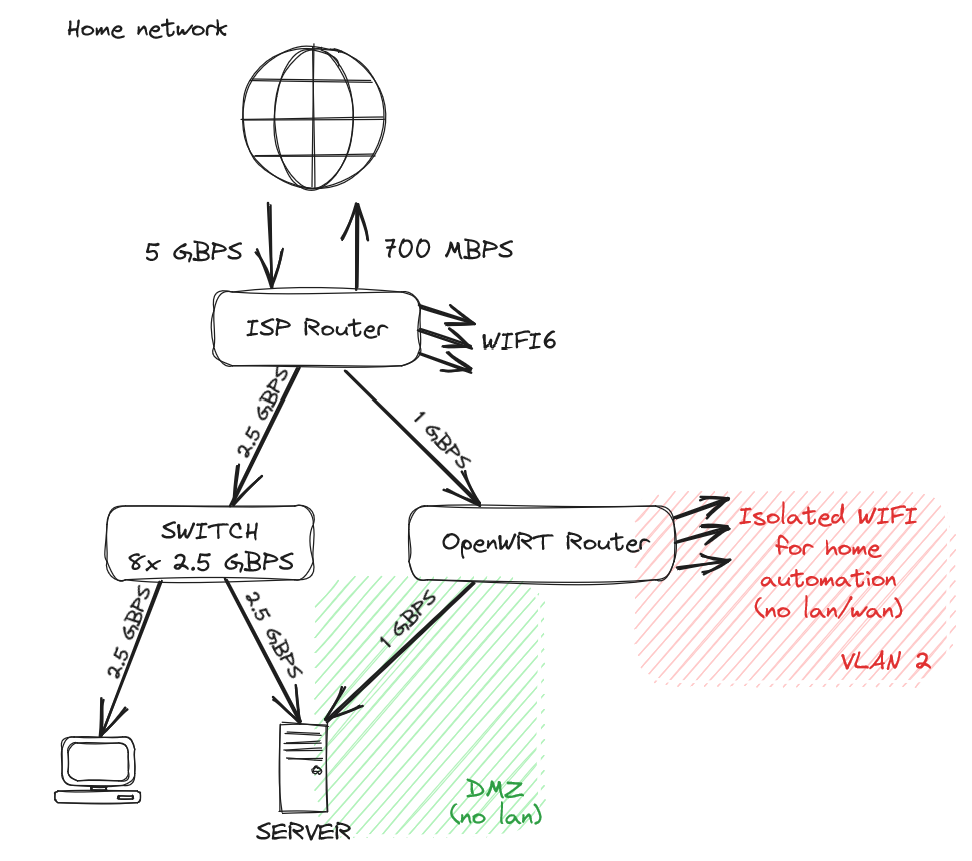
As an FYI: this set up is vulnerable to ARP spoofing. I personally wouldn’t use any ISP-owned routers other than for NAT.
Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
I'm not well versed in ARP spoofing attack and I'll dig around, but assuming the attacker gets access to a "public" VM, its only network adapter is linked to the openwrt router that has 3 separated zones (home lan, home automation, dmz). So I don't think he could have any impact on the lan? No lan traffic is ever going through the openwrt router.
The risk is the ISP Wi-Fi. As long as you’re using WPA with a good long random passkey, the risk is minimal. However, anyone who had access to your Wi-Fi could initiate an ARP spoof (essentially be a man-in-the-middle)
Well, to be honest if someone has access to my Wi-Fi, I'd consider that I've already lost. As soon as you're on my lan, you have access to a ton of things. With this setup I'm not trying to protect against local attacks, but from breaches coming from the internet
Doesn’t need to be the case if you segment your network to protect against ARP.
How would you change his setup to prevent ARP attacks? More network segmentation (clients and servers on separate VLANs) or does OPNsense additional protections I should look into?
I like the WiFi 6 just going out into the ether. Like you're just throwing morsels out to the peasants.
That’s… not all hand written is it? No one who is good at computers can write that well. We got into this BECAUSE we couldn’t write well, right?
Looks like excalidraw to me. I use it all the time to quickly make diagrams like these.
🙈
It's not, look at postgres under both DB in the last picture. That's not just the same writing, it's identical.
I would never use an ISPs router for my home network. It just causes so many issues that you can easily avoid by either using your own router directly or if that is not possible putting the device into "bridge" mode and using your own router behind it.
What are some of the issues?
The devices the ISPs send out are usually the cheapest hardware imaginable and therefore introduce substantial unnecessary latency.
Where I live some ISPs also used to use tools that genereted wifi passwords based on the devices MAC address. While this is apparently fixed now, a lot of non tech savvy users still use these old devices that are basically open to anyone now.
To save even more money, they sometimes deliberately send out faulty devices (as in devices that drop connection frequently, restart for no reason, etc) which is just horrible.
I know these issues because I worked in that field and there are a lot more unfortunately...
WIth my previous ISP, I swapped the ISP's router with my OpenWRT's and everything worked fine. With my current ISP, it appears that it's not that simple to swap the router altogether. But I'll be honest, the biggest factors are price and number of routers/switch. As I want 2.5gbps, I'd need a router with at least dual 2.5gbps ports. The WIFI6 offering is also quite nice. And if I can't swap my ISP router, it would just add another device. In a perfect world, I'd have a single router running openwrt, with wifi6 and couple of 2.5+gbps ports (but unfortunately openwrt doesn't play nice with most wifi6 routers and these routers can get very expensive) For now, my ISP router does the job and I haven't had any issue (yet)
You could spend a little for a prosumer router and AP. I have a very similar setup with a cable modem, edge router X (ubnt), a single UniFi AP, and a service running on my server (this could be replaced with a separate hardware device or Raspberry Pi, but the server is going to be running anyway). It's been rock solid since I set it up, compared to the WiFi/router combo with open-wrt I was running before that struggled and needed restarting regularly.
Not a net ops person but I had to change my WiFi router MAC to the one from the ISP to make it work
Also trying calling them, if you give them your mac they can put it in the system, and then it will work. Time Warner used to be big on mac filtering.
That is a great quality post! Congratulations and thank you
Your home network is not too shabby either ;)
I like the way you wrote this in history class
Congrats for keeping your setup simple!
Upvoting because Balsamiq
I'm afraid I can't take your upvote sir... excalidraw.com
Oh damn! I must be out of practice. Still a great tool
Hmm, nice detailed specs on your home network. Mind sharing your IP? For, uh... totally trustworthy reasons. Asking for a friend. >: )
192.168.0.1
Got it. Sending the virus to 192.168.0.1...
It’s been three months, I’m assuming the attack worked as intended lol
I heard everyone on the internet is nice and have good intentions. Did they lie to me?
Here's my password to show trust:
"*******"
You see, when you see 'hunter2', I only see '*******'
No no, it's Solarwinds123
Acronyms, initialisms, abbreviations, contractions, and other phrases which expand to something larger, that I've seen in this thread:
| Fewer Letters | More Letters |
|---|---|
| AP | WiFi Access Point |
| IP | Internet Protocol |
| NAT | Network Address Translation |
| SSD | Solid State Drive mass storage |
4 acronyms in this thread; the most compressed thread commented on today has 7 acronyms.
[Thread #100 for this sub, first seen 1st Sep 2023, 11:25] [FAQ] [Full list] [Contact] [Source code]
For the stupid among us, what’s the purpose of the switch?
Thank you for posting this with the explanations and great visuals! I am wanting to upgrade to a setup almost identical to this and you've basically given me the bill of materials and task list.
Anything you wish you had done differently or suggest changing/upgrading before I think about putting something similar together?
Very nice
Interesting setup, mines very similar. Except with ZFS and no DMZ 😅 I'm thinking of setting up vlans for automation too, how do you handle updates and software downloads on that lan?
If I ever need to update any device on the home automation vlan, I'd add an exception to the firewall for this specific host for the time of the update