Could someone please transcribe this? I can't be bothered to read it.
CameronDev
The stats are a sample, there is inheritantly some level of error. Ignore the month to month changes, focus on the longer term trends.
I miss when paywalls could be trivially bypassed by deleting the overlay
"Whoops, hope that wasn't mine"
Reset button not working, but power button working is quite odd.
Is it just the once that this happened? Can you reliably trigger it with the car charger? If yes, maybe worth plugging in a monitor while you triggering it and see what happens.
Are the server and chargers close to each other? Some kind of EMP effect? Seems unlikely, but who knows.
Cock wash?!
Careful, you'll get a hit piece put out on you
Looks like your time machine worked!
Maybe don't check Wikipedia, some things have changed....
This is well into paranoia territory. Anyone who is willing to either tail you until you have a medical episode or otherwise force the medical episode will have no trouble accessing your phone via more conventional means (kidnap + torture).
If you really want to protect against this "risk", either use a non-standard finger, or don't use biometrics at all.
And if you are likely to have a medical episode, either use your phones built in ICE (in case emergency) feature, wear one of those medical alert bands, or write the ICE numbers on your phone case.
Are you familiar with ReiserFS? Because that's how you get more ReiserFS's...

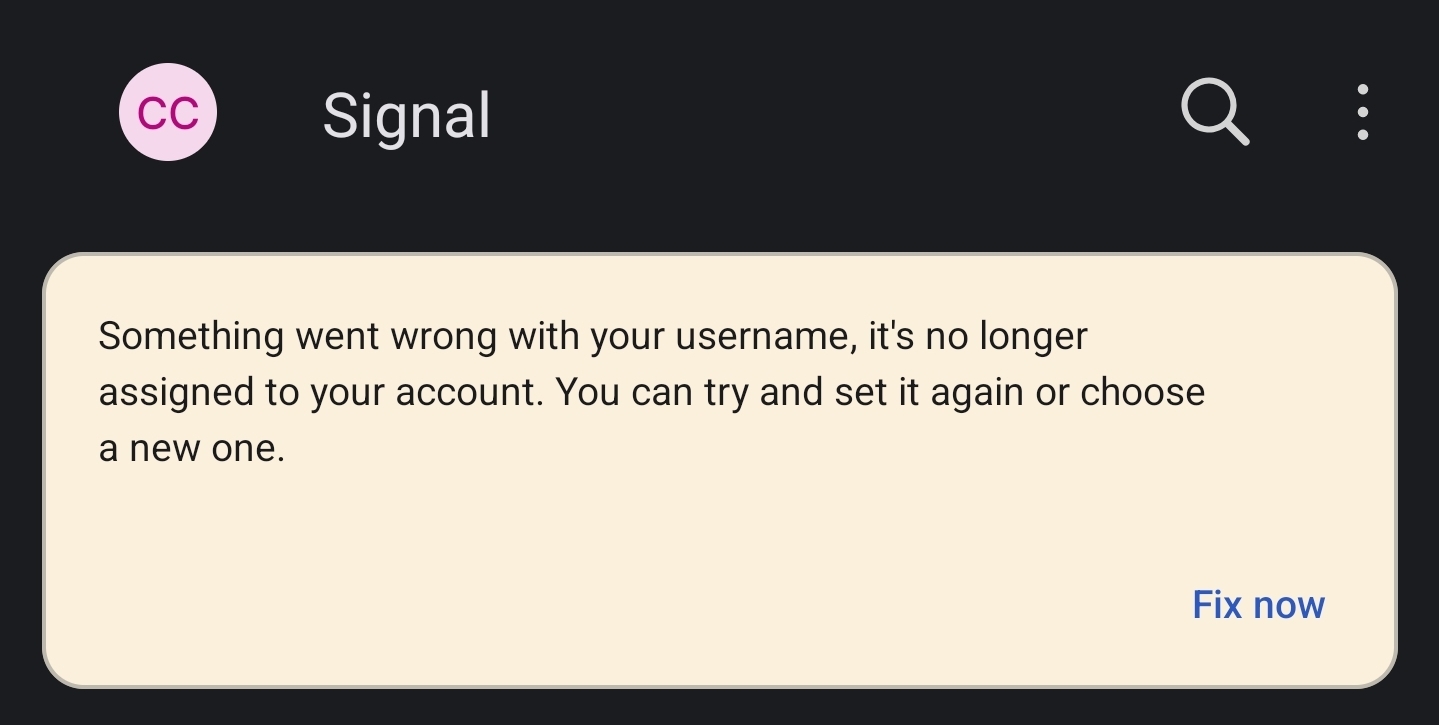
https://youtu.be/DHQRZXM-4xI
Follow that as you go through customs, and they'll wave you right through.