Time to use Framatalk instead of the main instance. Framatalk is an instance of Jitsi Meet.
citytree
Why would I use this ChatGPT thing when I can self-host Llama 2 or Falcon, which is free and open source?
Using git it’s probably the most easy and lightweight method to VC plain text ...
Really? I am currently using RCS for my simpler version control needs, and Git for larger and collaborative projects.
Behold the Rise of the Cybermen! Elon Musk is the John Lumic of our world. Humanity will be upgraded! https://piped.video/watch?v=TQs3gVobcfg
If you are unable to install a custom ROM on your Samsung smartphone, the next best alternative is probably to use https://github.com/0x192/universal-android-debloater to deactivate as much Google and Samsung spyware as possible.
Jami seems to have problems with message delivery. I was not able to send a message between my two Android phones. I have tried several times. Is anyone experiencing the same problem?
EDIT: here is a similar complaint: https://old.reddit.com/r/jami/comments/101cq00/why_is_jami_still_not_working/
Linux phones
Will we be able to use messaging apps such as WhatsApp and Signal on Linux phones?
Looking forward to greater support for "driverless printing" in more Linux distributions, especially via IPP-over-USB. This would allow most consumer-level printers to be used directly from Linux without needing proprietary drivers and/or explicit Linux support from the printer vendor. This solves one of the common pain points when using desktop Linux at home.
Why is Ecosia on the list?
Quoting from tosdr.org:
- This service can view your browser history
- This service may collect, use, and share location data
- This service allows tracking via third-party cookies for purposes including targeted advertising
- This service tracks which web page referred you to it
- Your personal data is given to third parties
Doesn't look privacy-respecting.
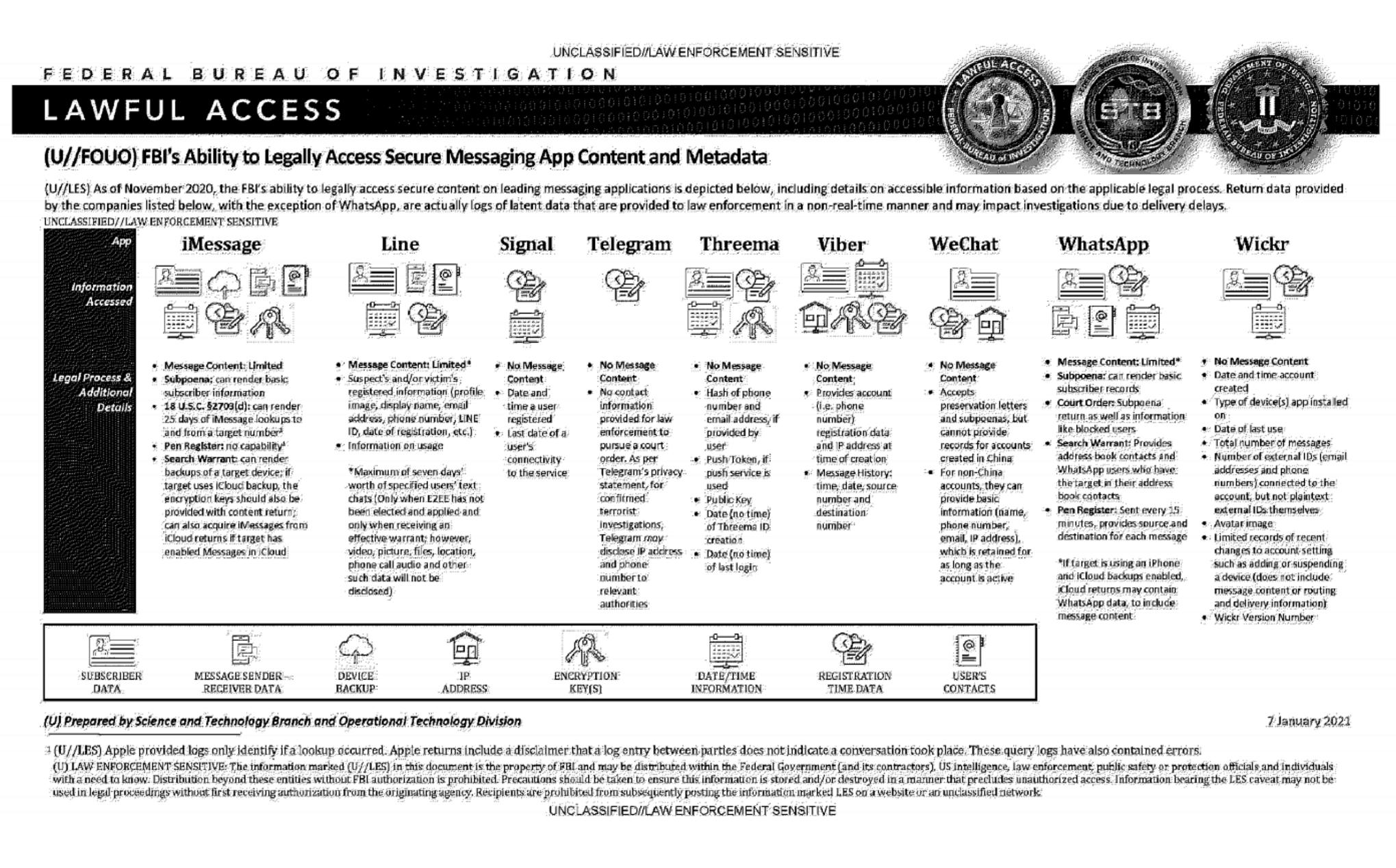
Thank you for the feedback. I have added additional information to the original post. I hope that the additional information answers all your questions.